The “Customizable Virtual Machine” feature, abbreviated as CVM, is the latest feature of NoirVisor developed in October, 2021. This feature aims to be the transition of the development focus of Project NoirVisor, making a regular security-research-purpose hypervisor to be also capable of running regular virtual machines so that its functionality could be even more powerful.
Architecture
The architecture of NoirVisor CVM is based on the hypervisor framework from NoirVisor. In other words, the host is also running in a virtualized environment. In this regard, the system can run virtual machines without conflicting security features that utilize virtualization.
Regular security-research hypervisors have only one VMCS or VMCB, which represents the physical processor of the subverted host, per processor. NoirVisor, however, has a mechanism to switch the VMCS or VMCB to be scheduled onto the physical processor. These additional VMCSes or VMCBs represent the vCPUs of the guest.
The condition to switch from the host to the guest is the call of running a vCPU. When this condition is met, the state of host processor is saved. After saving the processor state, NoirVisor loads the state of the guest, and finally executes the specific instruction (vmlaunch, vmresume or vmrun) to run the vCPU.
The condition to switch from the guest to the host is the VM-Exit happened in the vCPU. Depending on the reason of VM-Exit, NoirVisor may either forward the exit to the user hypervisor if the user hypervisor specified to intercept so, or process the VM-Exit on its own.
Introductory Guide of CVM Programming
The following image illustrates a high-level overview of NoirVisor CVM programming architecture.
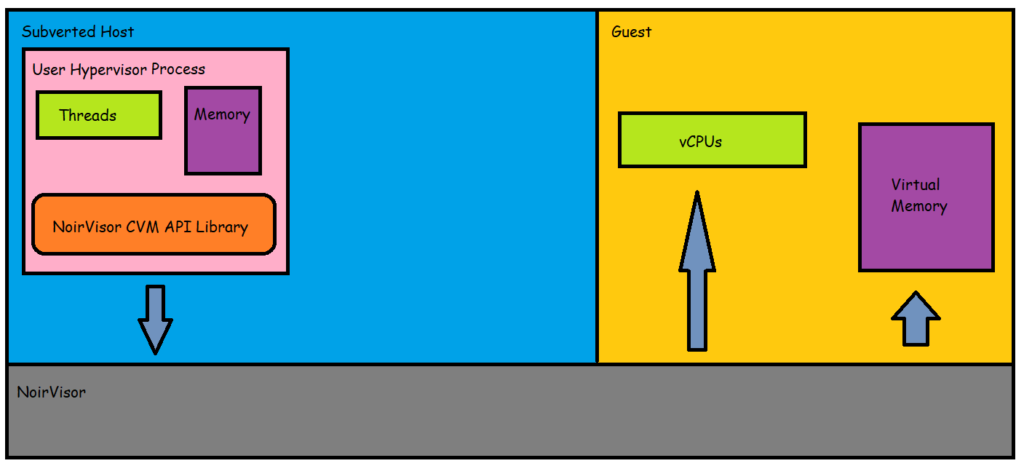
Certain notations must be explicated.
User Hypervisor is a process that hosts the guests. The vCPUs and the virtual memory of the guest are given by the User Hypervisor.
Guest is the synonym of a virtual machine.
A vCPU – alias for virtual processor, evident from its name – is a processor of the virtual machine. To run a vCPU, the User Hypervisor should provide a thread for it.
The virtual memory is the memory of the guest. To provide memory for the guest, the User Hypervisor must map them accordingly.
The general workflow of CVM programming will start by creating virtual machines and their corresponding virtual processors, mapping the virtual memory to the guest and initializing the states of the processor. The memory contents must be initialized as well, or where the code will be executed otherwise?
During the execution, the vCPU may trigger VM-Exits that require User Hypervisor to handle. This typically could be conditions intercepted by NoirVisor. For example, if the vCPU executes an out instruction, then an I/O-intercept VM-Exit will be triggered. User Hypervisor must emulate the I/O operation for the guest.
When the guest is going to shutdown, the User Hypervisor should delete the virtual machine. In addition to that, other resources (e.g: virtual memory, file handle, etc.) used for the guest must be released for the sake of resource-leak elimination.
For further details of how to use the APIs, visit the NoirCvmApi Wiki.
If you have difficulties playing with the APIs, feel free to submit an issue.
Work in Plan
The NoirVisor CVM lacks support to Intel VT-x. The development is at debugging stage. However, for some arcane reasons, a guest cannot be launched properly. I am currently investigating the issue.
The NoirVisor has a project to port itself to UEFI. Once it is done, NoirVisor may provide hypervisor functionality to the host OS so that Hyper-V or some other stuff may be running with NoirVisor CVM.
Perhaps, the VMware may join the community of NoirVisor CVM. This is literally a daydream of mine, but who knows anyway? Project NoirVisor needs some reputations.
Leveraging the Secure Encrypted Virtualization is planned. However, it requires interactions with AMD-SP, which is an external PCI device in the system. Interaction with AMD-SP will not be a part of SVM-Core in that the SVM-Core is supposed to be CPU-driven.
Conclusion
Although the current implementation of NoirVisor CVM looks like a toy for virtualization enthusiasts and hobbyists looking for a playground for developing virtual machines, I definitely want to make it possible to be applied in consumer and business market.
Feel free to visit the open-source Project NoirVisor.